In a world where data security is essential, enabling MongoDB SSL is critical in fortifying your database. This guide walks you through implementing SSL/TLS encryption for MongoDB. Each section is crafted to elevate your database’s security protocol, from acquiring the necessary SSL certificates to configuring server and client connections.
Key Takeaways
- SSL/TLS encryption is essential for securing data transfer in MongoDB, which supports Forward Secrecy and has undergone configuration changes reflecting security advancements since version 3.0.
- To set up SSL/TLS encryption, one must obtain valid SSL certificates from a Certificate Authority or create self-signed certificates and then prepare them in the .pem format required by MongoDB.
- Configuring MongoDB server for SSL/TLS involves modifying the mongod.conf file with SSL settings, including specifying paths to .pem files and enabling certificate validation to ensure only trusted clients can connect.
Understanding MongoDB TLS SSL Encryption
Firstly, we need to understand the significance of SSL/TLS encryption in MongoDB. This encryption is not just a layer of protection; it’s the cornerstone of secure data transfer in MongoDB, ensuring that your data remains unintelligible to unauthorized entities even if intercepted.
MongoDB, including its managed service Atlas, employs this encryption to safeguard connections, starting from version 3.0 and onwards, supporting cipher suites that enable Forward Secrecy for an even stronger defense against eavesdropping. But as with all technology, evolution is constant. MongoDB’s SSL/TLS configuration options have undergone significant changes across versions.
The switch from old TLS flags to new ones and the default use of the Online Certificate Status Protocol (OCSP) to verify certificate status in later versions reflect MongoDB’s commitment to staying ahead of the security curve. Being aware of these changes enables you to use TLS/SSL connections effectively and maintain the privacy of your MongoDB instance in the digital age.
Preparing SSL Certificates for MongoDB
The SSL certificates are necessary for our MongoDB server to establish secure SSL/TLS communications. These certificates are like digital passports, asserting the identity of our server to clients in the vast digital expanse.
Obtaining these valid certificates is the first step to establishing a secure communication channel. Should your circumstances dictate, you may create a self-signed certificate, acting as your own Certificate Authority. This approach is particularly useful in testing or development environments.
Obtaining SSL Certificates from a Certificate Authority
You must approach a trusted certificate authority to obtain a server certificate that verifies your server’s identity. This process begins with an OpenSSL configuration file, a blueprint containing details like your country, state, and organization, capped with the common name that is your server’s alias.
Once you’ve crafted this foundation, a Certificate Signing Request (CSR) emerges, which you’ll present to the certificate authority, much like a knight presenting a decree to a king.
The CA, in turn, grants you a valid certificate, a seal of trust that assures clients your server is legitimate. But the journey doesn’t end there; you must ensure this valid certificate is compatible with MongoDB and recognized by the clients connecting to your server, thus completing the circle of trust.
Creating Self-Signed Valid Certificates
If obtaining a certificate from a trusted authority isn’t feasible, you can create your self-signed certificate. This requires generating a CA private key, the start of your self-signed certificate, using the openssl genrsa command. This key serves as the foundation for creating your own CA certificate, which will, in turn, be used to sign an intermediate certificate.
The process continues by combining the self-signed CA certificate and private key into a single .pem file. This file becomes the server’s identity, ready to be presented to any client that wants to connect, ensuring the protection of the client’s identity and maintaining the integrity of the server’s identity.
Further reading:
MongoDB SSL with Self-Signed Certificates in Node.js
MongoDB® SSL with Self-Signed Certificates in C#
Configuring MongoDB Server for SSL/TLS Encryption
Once your certificates are ready, the next step is configuring the MongoDB server for SSL/TLS encryption, allowing you to securely connect to MongoDB. This procedure involves opening MongoDB’s configuration file, typically known as mongod.conf. Here, you’ll add the path to your .pem file, setting the stage for encrypted connections. As you add the ssl.PEMKeyFile option into the configuration, the server takes its first steps towards securing its communications.
If your private key is password protected, you’ll access it with the sslPEMKeyPassword option, ensuring that only those with the secret passphrase can access it.
Setting Up mongod and mongos with SSL/TLS Certificate and Key
Setting up mongod and mongos with the SSL/TLS certificate and key is a process that requires attention to detail. In the configuration file, the following steps need to be taken:
- Set net.ssl.mode to requireSSL.
- Direct net.ssl.PEMKeyFile to the path of your .pem file.
- Set net.ssl.CAFile option to point towards the root certificate chain .pem file, ensuring that the entire line of trust is established.
Enabling Client Certificate Validation for mongod and mongos
In MongoDB, enabling certificate validation for mongod and mongos ensures that every client presents a valid certificate, serving as a trusted delegate of the Certificate Authority.
This is achieved by setting the net.ssl.CAFile option with the path to the .pem file that contains the root certificate chain. By setting the net.ssl.mode to requireSSL and disallowing invalid hostnames, you affirm the authenticity of each client’s identity, strengthening the walls of your MongoDB fortress.
Any client that fails to present a valid SSL certificate finds their access denied, as the server rejects connections that cannot trace their lineage back to the trusted Certificate Authority.
Implementing FIPS Mode for MongoDB
Venturing further into security, we encounter the Federal Information Processing Standards (FIPS) mode. This standard is not just a set of guidelines but a certification that MongoDB proudly supports.
Integrating FIPS mode with SSL/TLS libraries ensures that network encryption and authentication mechanisms adhere to the highest security guidelines, a requirement for many government and regulated industries.
MongoDB’s embrace of FIPS mode with OpenSSL3, starting in version 6.0.7, showcases its dedication to providing a secure environment on select operating systems like Ubuntu 22.04, RHEL 9, and Amazon Linux 2023.
Configuring MongoDB Clients for SSL/TLS Encryption
With our server now securely encrypted, it’s time for our clients to do the same. Configuring MongoDB clients for SSL/TLS encryption is pivotal in ensuring end-to-end security. Properly adjusting your SSL settings will help maintain a secure connection.
Connecting via the MongoDB Shell with SSL/TLS
The Mongo shell can connect to the server using SSL/TLS by invoking the ‘–tls’ flag. For versions of the shell before 4.2, the ‘–ssl’ flag serves the same purpose. The shell also has options like ‘–tlsCertificateKeyFile’ and ‘–tlsCAFile’, allowing it to present its SSL/TLS credentials and recognize the trusted Certificate Authority, respectively.
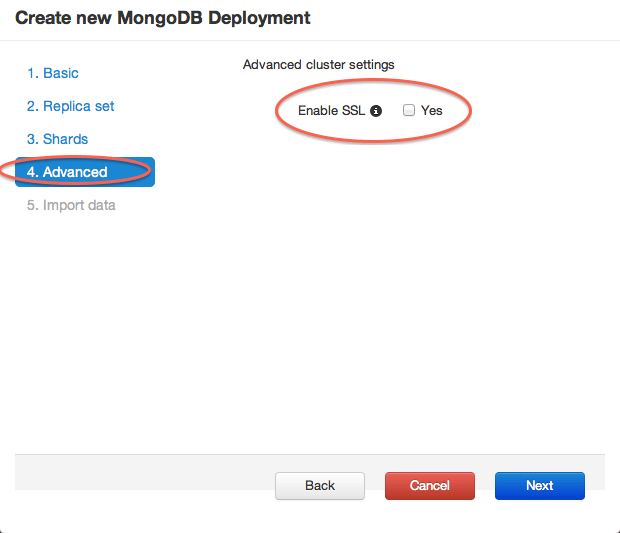
How to Enable SSL for MongoDB on ScaleGrid Console
Enabling SSL is now as easy as checking a box in the MongoDB creation wizard:
So Why Use SSL with MongoDB®?
Privacy
If you’re connecting to your MongoDB server over unsecured networks, your data travels unencrypted and is susceptible to eavesdropping and tampering. SSL encrypts the data so only the two endpoints can access the unencrypted data.
Authentication
Use PKI (private key infrastructure) to ensure that only clients with certificates from an appropriate CA can connect to the MongoDB server. This is an additional step, and you can choose not to use your custom certificates or CA – you’ll still have the benefits of privacy due to end-to-end encryption.
MongoDB SSL Drawbacks
Performance Overhead
There’s some performance overhead for using SSL. While we’re yet to run comprehensive tests, there is definite overhead due to using SSL.
Lack of MongoDB UI
The most popular MongoDB UIs don’t support SSL out of the box. So, you might need to go for the paid version or use the mongo console.
Connecting to your SSL-Enabled MongoDB Server
If you’re connecting to a MongoDB server with SSL enabled, several differences exist in the MongoDB connection code. Please refer to the documentation of your driver for more details.
Mongo Shell
The default mongo client does not support connections to an SSL enabled server – you need the SSL enabled-build of MongoDB. You can SSH into the SSL enabled server and then use the mongo client on the server to connect. Here is the syntax to connect using the admin user provided by ScaleGrid:
mongo --ssl --sslCAFile <file.crt> -u admin -p <pass> servername/admin
Code
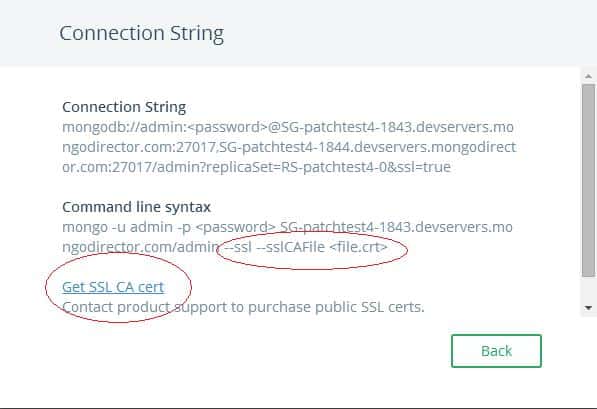
You must append the “ssl=true” property to your MongoDB connection string. Also, certain platforms (e.g. JDK) will require you to add the public key of the SSL certificate to the trusted path before you can connect to the server. By default, a self-signed certificate is generated for every cluster.
You can download the public key of the SSL certificate from the UI or the certificate from /etc/ssl/mongodb-cert.crt on the server. In the UI, a link to download the SSL public cert is available in the connection string modal:
For more instructions on how you can SSH into the instance, refer to the “VM Credentials” section in this blog post. The crt file is located at /etc/ssl/mongodb-cert.crt on the server. Once you’ve downloaded the public key, you’ll need to add it to your trusted keystone:
keytool -import -alias "MongoDB-cert" -file "/etc/ssl/mongodb-cert.crt" -keystore "/usr/java/default/jre/lib/security/cacerts" -noprompt -storepass "changeit"
The default password for the cacerts store is “changeit”. For security reasons, you should change this password to your own. Once you’ve added the certificate, enumerate the certs in the keystone to confirm that the certificate got added:
keytool -list -keystore cacerts -storepass changeit
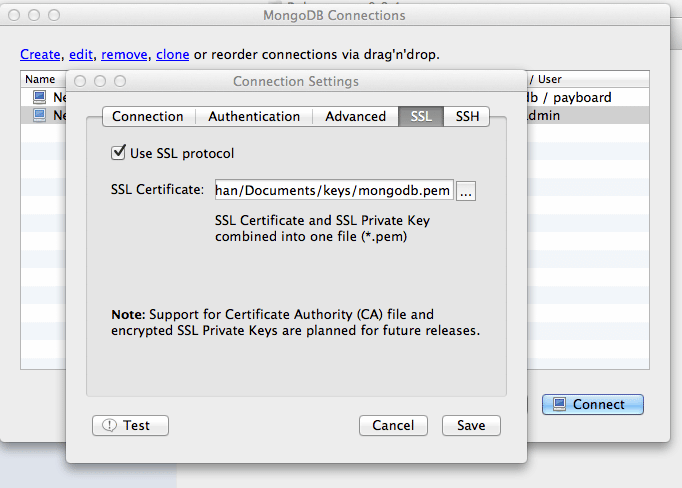
Mongo UI: Robo 3T
Robo 3T (formerly Robomongo) is one of the few MongoDB UIs that support connecting with SSL. When creating a connection to your MongoDB server, select the SSL option. For the certificate, use the .pem file with both the public and private keys. This file is located at /etc/ssl on your MongoDB server. Check out our Robo 3T MongoDB Connection Guide for more details.
Best Practices for TLS SSL Configuration
Reflect on the best practices for maintaining a robust MongoDB TLS/SSL configuration. Here are some essential practices to follow:
- Get rid of outdated and vulnerable protocols like SSLv3 and early versions of TLS to fortify your defenses.
- Embrace certificates from trusted certificate authorities to ensure secure communication.
- Implement perfect forward secrecy to protect against decryption of past communications.
By following these practices, you can strengthen the security of your MongoDB deployment.
Frequently Asked Questions
Does MongoDB use SSL?
Yes, MongoDB can use SSL with any valid TLS/SSL certificate issued by a certificate authority or a self-signed certificate. However, if a self-signed certificate is used, the server identity is not validated.
How to disable SSL in MongoDB?
To disable SSL in MongoDB, you can edit the Mongo config file to set ‘ssl: mode: disabled’ and then restart the Mongod process. This will effectively disable SSL.